Take the time to go over this HIPAA Security Rule Checklist in full and be sure to involve all parties with knowledge of each area before checking off the boxes. It applies to electronic protected health information ePHI which should be protected if it is created maintained received or used by a covered entity.
 What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
What Is Hipaa Compliance Hipaa It Requirements Dnsstuff
6 audits must be performed each year.
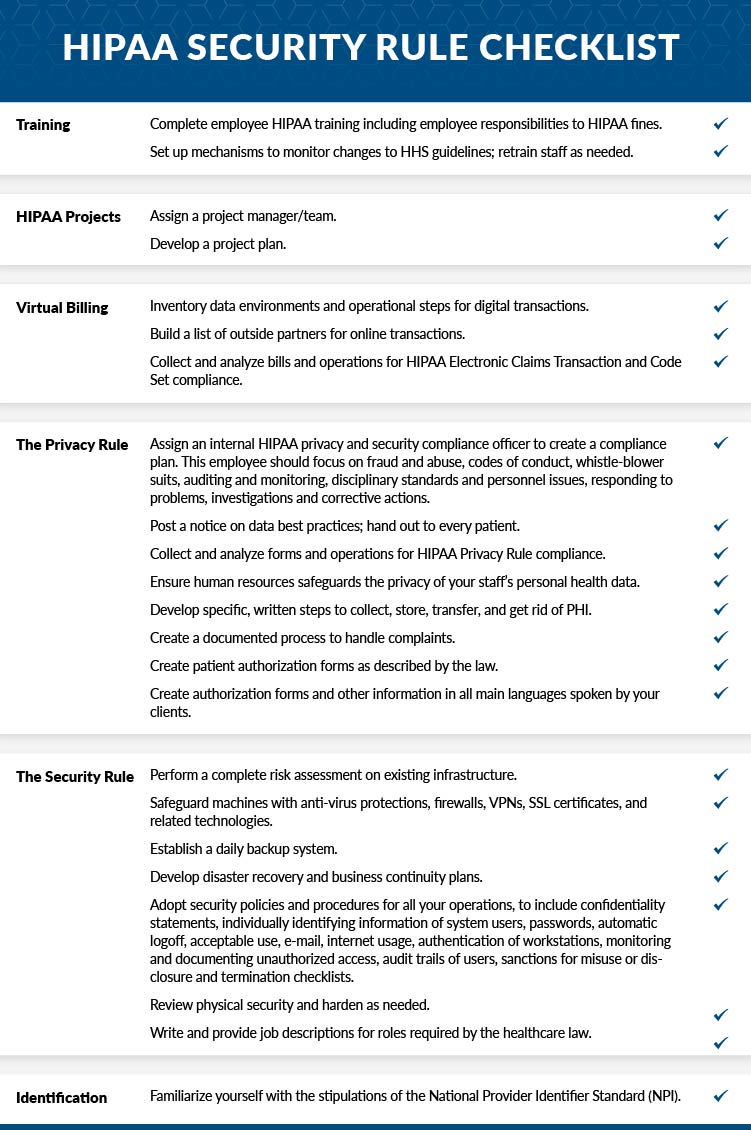
Hipaa security rule checklist. HIPAA cybersecurity is an ongoing process not a one-time investment. The HIPAA Security Rule Checklist broken down into specific categories is below. HIPAA security requirements are vague this is intentional but every CE and BA with.
This HIPAA Security Compliant Checklist is provided to you by. HIPAA Security Guidance HHS has developed guidance and tools to assist HIPAA covered entities in identifying and implementing the most cost effective and appropriate administrative physical and technical safeguards to protect the confidentiality integrity and availability of e-PHI and comply with the risk analysis requirements of the Security Rule. IHS HIPAA Security Checklist summarizes the specifications and indicates which are required and which are addressable.
Government mandates that certain precautions must be taken to ensure the safety of sensitive data. HIPAA Security Suite has years of experience teaching practices on how to improve cybersecurity. Another good reference is Guidance on Risk Analysis Requirements under the HIPAA Security Rule.
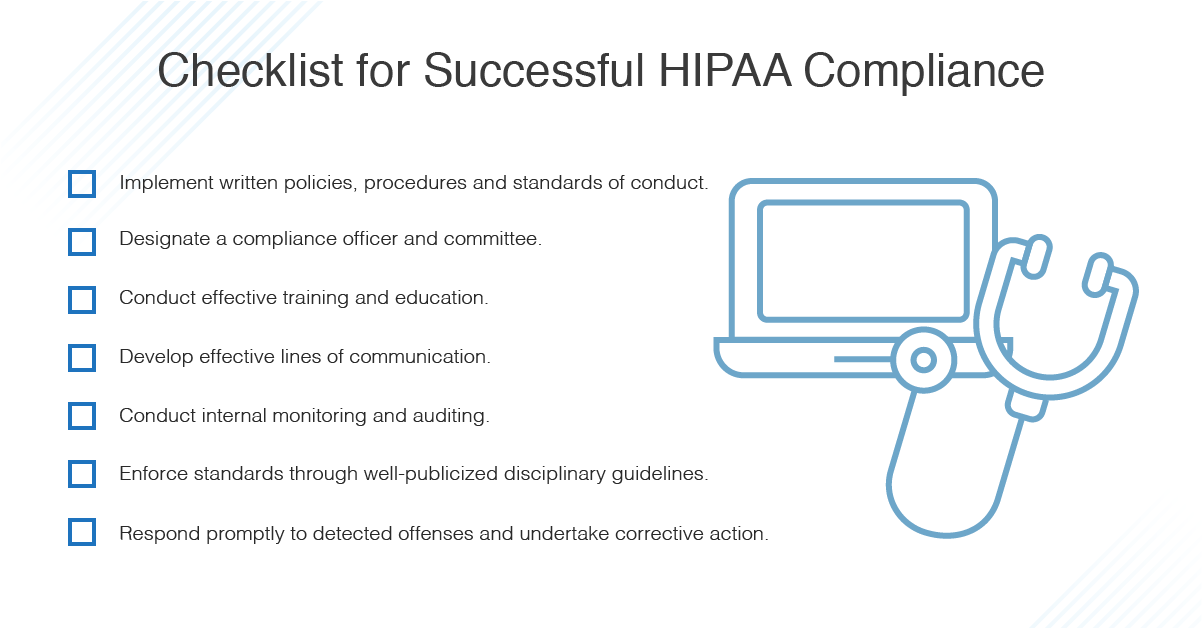
If you are preparing a HIPAA security rule checklist you should add several things in it to authorize it. The HIPAA security rule primarily governs personal information protection ePHI by setting standards to protect this electronic information created received used or retained by a covered entity. The safeguards of the HIPAA Security Rule are broken down into three main sections.
You can use the checklist below to perform an internal audit. The HIPAA Privacy Rule defines PHI as individually identifiable health information stored or transmitted by a covered entity or their business associates. Introduction to the HIPAA Security Rule Compliance Checklist.
As the official title of the HIPAA Security Rule suggests the HIPAA Security Rule was created in order to define the exact stipulations required to safeguard electronically Protected Health Information ePHI. Your HIPAA Security Checklist. Since its adoption the rule has been used to manage.
The security rule identifies three specific safeguards administrative physical and technical to ensure data security and regulatory compliance. A HIPAA security checklist can help you identify where your business operations fail to meet HIPAA privacy requirements. The Security Rule Checklist is what some may call a security risk assessment but it is only part of a full HIPAA Risk Analysis.
If your organization works with ePHI electronic protected health information the US. The Security Rule The HIPAA Security Rule outlines specific regulations that are meant to prevent breaches in the creation sharing storage and disposal of ePHI. The HHS has produced seven education papers designed to teach entities how to comply with the security rules.
The HIPAA Security Rule is a subset of the HIPAA Privacy Rule. Government mandates that certain precautions must be taken to ensure the safety of sensitive data. Or you can use the checklist as a way to gauge how seriously your organization takes HIPAA compliance.
Both covered entities and business associates must comply with the Security. The HIPAA Security Rule was created by the US Department of Health and Human Services as a set of standards that serve to improve the security of ePHI and their confidentiality integrity and availability both in rest and in transit. The HIPAA Compliance Checklist.
In other words the Security Rule regulates how this information is stored secured and transmitted between electronic devices. For an approach to the addressable specifications see Basics of Security Risk Analysis and Risk Management. What are the HIPAA Security Rule Checklist Categories.
The HIPAA Security Rule comprises three pillars of safeguards that encompass the necessary controls and procedures prescribed in HIPAA. Auditing reassessing and continuing education are all essential to keeping patients safe. The penalties for not complying with these legal requirements set forth by HIPAA can be severe.
For example you should add a note on permission health data the reason for the disclosure etc. Or you can just click on the download button to have those all aspects by making a checklist in numbers. The third action item in your HIPAA compliance checklist is knowing what types of patient data you need to protect and begin putting the right security and privacy measures in place.
The Security Rule Electronic Protected Health Information. The HIPAA Security Rule establishes standards for the protection of Electronic Protected Health Information EPHI. HIPAA Security Rule Checklist.
HIPAA Security Rule Checklist.