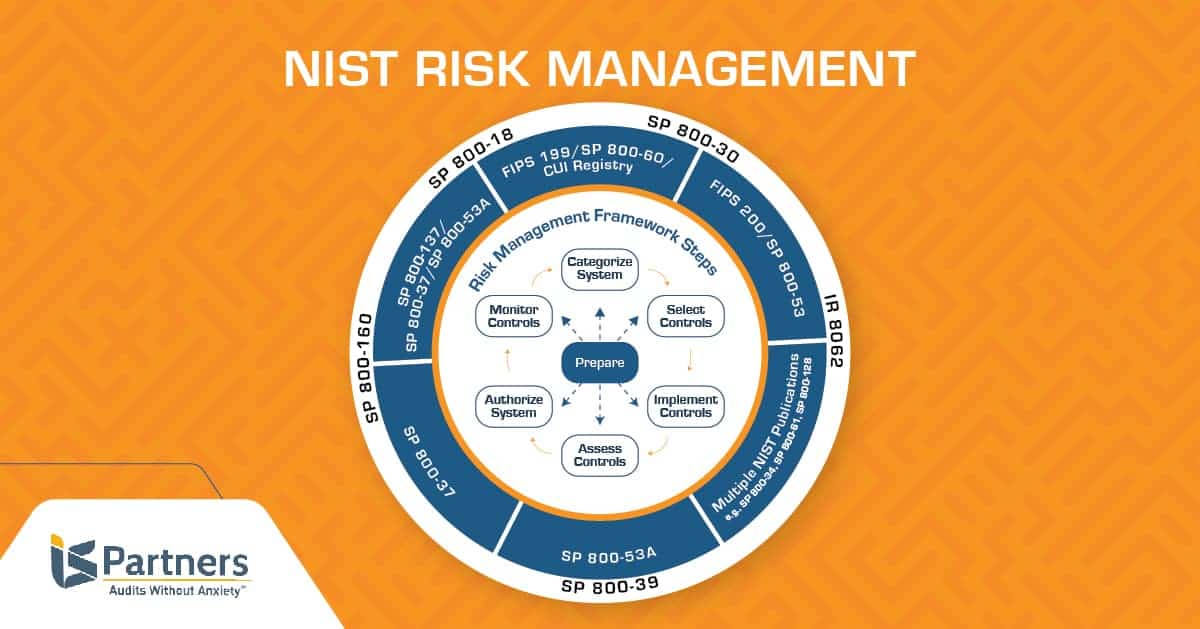
The Risk Management Framework RMF is a set of information security policies and standards the federal government developed by The National Institute of Standards and Technology NIST. The RMF is explicitly covered in the following NIST publications.
 Tips For Preparing Your Next Nist Risk Assessment I S Partners
Tips For Preparing Your Next Nist Risk Assessment I S Partners
Bring together all of the.

Nist risk management framework. The integration of privacy risk management processes. An alignment withsystem life cycle security engineering processes. The risk-based approach to control selection and specification considers effectiveness efficiency and constraints due to applicable laws directives Executive Orders policies standards or regulations.
The PNT Profile was created by using the NIST Cybersecurity Framework and can be used as part of a risk management program to help organizations manage risks to systems networks and assets that. The risk-based approach to control selection and specification considers effectiveness efficiency and constraints due to applicable laws directives Executive Orders policies standards or regulations. An introduction to the NIST Risk Management Framework.
Recognized In Every Major Market The FRM Is The Leading Certification For Risk Managers. Ad Assess risk create your risk registry plan mitigations and perform management reviews. NIST Risk Management Framework RMF.
The Risk Management Framework NIST Special Publication 800-37. Recognized In Every Major Market The FRM Is The Leading Certification For Risk Managers. If your resource qualifies and you would like it listed at the Framework Industry Resources Web page send a description of your resource to cyberframeworknistgov.
Risk Management Framework first documented in NIST Special Publication 800-37 was developed by NIST in 2010 as a key element of the FISMA Implementation. Not only is this framework universal and comprehensive but it can also be easily explained at a high level to the C-Suite and Board aiding in collaboration between internal audit and management. Representations and Warranties Certain commercial entities equipment or materials may be identified in this Web site or linked Web sites in order to support Framework understanding and use.
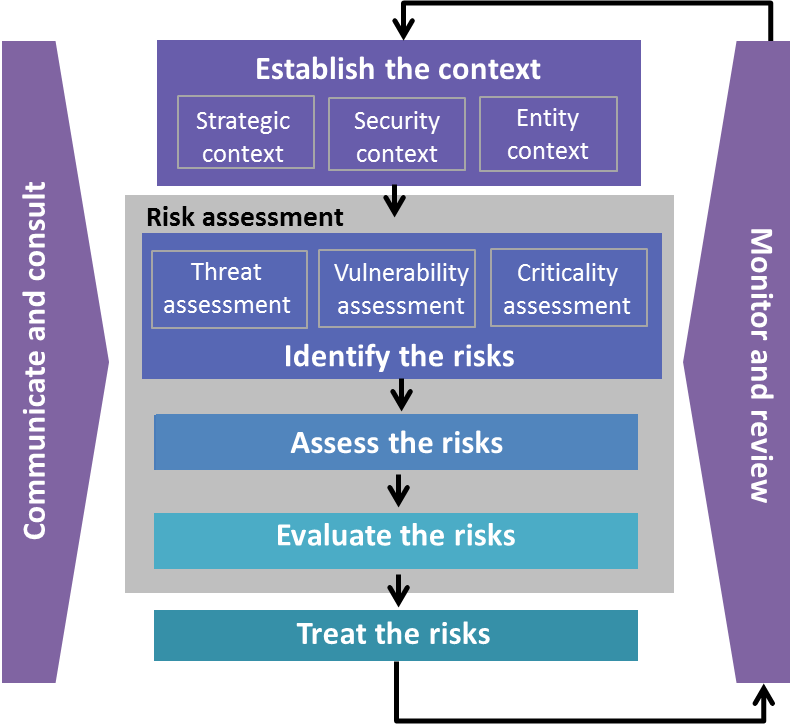
And the incorporation of supply chain risk management processes Organizations can. The updates include an alignment with the constructs in the NIST Cybersecurity Framework. The Risk Management Framework provides a process that integrates security privacy and risk management activities into the system development life cycle.
The NIST Risk Management Framework RMF provides a comprehensive flexible repeatable and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal. NIST Risk Management Framework Overview About the NIST Risk Management Framework RMF Supporting Publications The RMF Steps. The Risk Management Framework provides a process that integrates security privacy and cyber supply chain risk management activities into the system development life cycle.
Ad Assess risk create your risk registry plan mitigations and perform management reviews. Ad Navigate Uncertain Times Get Financial Risk Manager FRM Certified. ENHANCED RISK MANAGEMENT NIST develops frameworks to help measure and manage cybersecurity and privacy risks in the larger context of an enterprise.
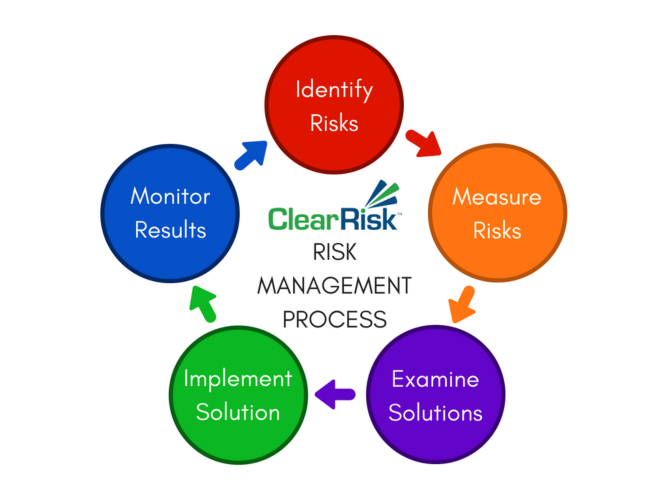
Risk management solution to identify analyze prioritize and respond to risks. Risk management solution to identify analyze prioritize and respond to risks. NIST is pleased to announce the release of NISTIR 8323 Foundational PNT Profile.
Monitor Additional Resources and Contact Information NIST Risk Management Framework 2. The Risk Management Framework RMF to. The NIST Cybersecurity Risk Management Framework delivers on both.
The Cybersecurity Framework CSF to help organizations understand and address risks with a flexible approach that offers a common language. Applying the Cybersecurity Framework for the Responsible Use of Positioning Navigation and Timing PNT Services. Projects NIST Risk Management Framework About the RMF.
Ad Navigate Uncertain Times Get Financial Risk Manager FRM Certified. The Risk Management Framework is a United States federal government policy and standards to help secure information systems computers and networks developed by National Institute of Standards and Technology. System Risk Management Framework NIST Special Publication 800-39 Enterprise-Wide Risk Management NIST Special Publication 800-53 Recommended Security Controls NIST Special Publication 800-53A Security Control Assessment NIST Special Publication 800-59 National Security Systems NIST Special Publication 800-60 Security Category Mapping Many other FIPS and NIST.