Since the other steps depend on this being done correctly it is important to identify all policies procedures and information types. Cybersecurity Risk Management Framework RMF.
 Nist Rmf Automation Risk Management Framework Xacta Telos Corporation
Nist Rmf Automation Risk Management Framework Xacta Telos Corporation
As you step through the risk management process review activity questions will appear for you to answer.
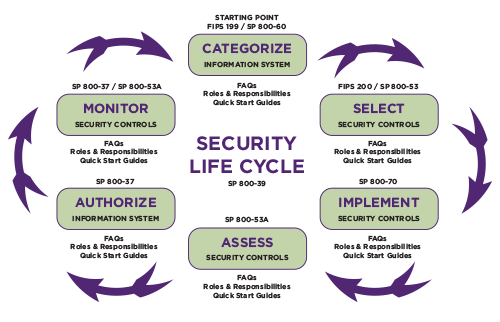
Rmf process steps. RMF is a risk management framework used primarily by the Department of Defense and the US government. It is defined by NIST 800-37 the latest revision is version two which you can see in the top of the PowerPoint page here the presentation. The Six Steps of the Risk Management Framework RMF The RMF consists of six steps to help an organization select the appropriate security controls.
Monitor Additional Resources and Contact Information NIST Risk Management Framework 2. In this blog post Lon Berman CISSP talks about the sub-steps of the first RMF step System Categorization. The BSI risk management framework Figure 1 shows the RMF as a closed loop process with five basic activity stages.
Ad Trackwell offers VMS Services for EEZ Monitoring cloud based or locally hosted. If playback doesnt begin shortly try restarting your device. The process has six main steps and were going to go through those steps at a very high level.
Throughout the application of the RMF measurement and reporting activities occur. You are overseeing the risk management process for the implementation of an information system with a small user base at your organization. The first and perhaps most important step in the system categorization process is the determination of the information types that are stored and processed by the system.
All information that is processed stored and transmitted on the system must be categorized using the new security objectives and impact levels. The RMF breaks down these objectives into six interconnected but separate stages. Integration of the RMF in acquisition processes reduces required effort to achieve.
Risk Management Frame RMFUnderstanding the RMF Steps. Categorize the information system and the information processed stored and transmitted by that system based on an impact analysis. Ad Trackwell offers VMS Services for EEZ Monitoring cloud based or locally hosted.
Cybersecurity RMF steps and activities as described in DoD Instruction 851001 should be initiated as early as possible and fully integrated into the DoD acquisition process including requirements management systems engineering and test and evaluation. Vested party is identified. When you answer a question correctly the risk level associated with your information system lowers.
System categorization is the first step in the six steps to RMF implementation. The RMF steps include. NIST Risk Management Framework Overview About the NIST Risk Management Framework RMF Supporting Publications The RMF Steps.
RMF Step 1 Categorize Information System. The 6 Risk Management Framework RMF Steps At the broadest level RMF requires companies to identify which system and data risks they are exposed to and implement reasonable measures to mitigate them. FISMA Background About the RMF Prepare Step Categorize Step Select Step Implement Step Assess Step Authorize Step Monitor Step SP 800-53 Controls Release Search Downloads Control Overlay Repository Overlay Overview SCOR Submission Process SCOR Contact RMF Introductory Course RMF Email List Meet the RMF Team.
These activities focus on tracking displaying and understanding progress regarding software risk. RMF Step 2Select Security Controls.