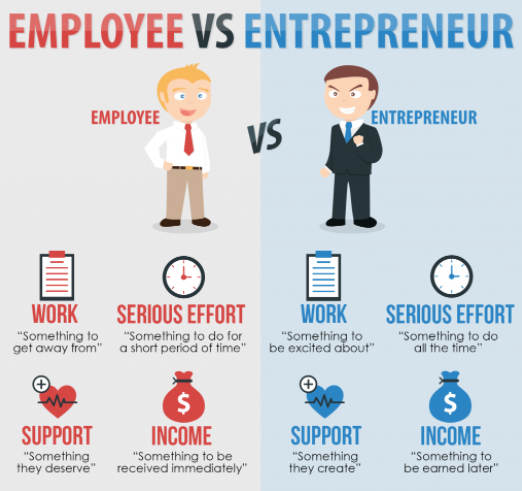
Control selection implementation. The RMF provides a disciplined structured and flexible process for managing security and privacy risk that includes information security categorization.
 Managing Information Security Risk Nist Sp 800 39 National Institute Of Standards Technology 9781796891980 Amazon Com Books
Managing Information Security Risk Nist Sp 800 39 National Institute Of Standards Technology 9781796891980 Amazon Com Books
NIST Risk Management Framework 5 Three Levels of Organization -Wide Risk Management.

Nist 800 39. 1 While agencies are required to follow NIST guidance in accordance with OMB policy there is flexibility within NISTs guidance in how agencies apply the guidance. NIST SP 800-39. Special Publications SPs are developed and issued by NIST as recommendations and guidance documents.
Attribution would however be appreciated by NIST. Special Publication 800-39 provides a structured yet flexible approach for managing information security risk that is intentionally broad-based with the specific details of assessing responding to and monitoring risk on an ongoing basis provided by other supporting NIST security standards and guidelines. For other than national security programs and systems federal agencies must follow those NIST Special Publications mandated in a Federal Information Processing Standard.
A System Life Cycle Approach for Security and Privacy. In accordance with the provisions of FISMA 1. NIST Special Publication 800-39 was developed to provide guidance for an integrated organization-wide program for managing information security risk to organizational operations organizational assets individuals other organizations and the Nation resulting from the operation and use of federal information systems.
National Institute of. Organization Mission and Information System View. Risk Framing 25 NIST SP 800-39.
Risk Management Framework for Information Systems and Organizations. Special Publication 800-39 Managing Information Security Risk Organization Mission and Information System View Compliance with NIST Standards and Guidelines. This document provides guidelines developed in conjunction with the Department of Defense including the National Security Agency for identifying an information system as a national security system.
This publication is available free of charge from. GitHub has enabled NIST to engage the community in near-real-time to more efficiently create a better product. FIPS 200 mandates the use of Special Publication 800-53 as amended.
The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing visibility into organizational assets awareness of threats and vulnerabilities and visibility into the effectiveness of deployed security controls. Risk Framing Establishes the context and provides a common perspective on how organizations manage risk Risk framing produces a risk management strategy that addresses how organizations intend to Assess risk Respond to risk and Monitor risk. The purpose of Special Publication 800-30 is to provide guidance for conducting risk assessments of federal information systems and organizations amplifying the guidance in Special Publication 800-39.
NIST Special Publication 800-39 Managing Information Security Risk. Unless otherwise specified by OMB the 800-series guidance documents published by NIST generally allow agencies some latitude in the application. NIST SP 800-39.
Department of Commerce. The Secretary of Commerce shall on the basis of standards and guidelines developed by NIST prescribe standards and guidelines pertaining to. 800-63-3 73 pages June 2017 CODEN.
The NIST SP 800-39 Risk Management Process. Risk assessments carried out at all three tiers in the risk management hierarchy are part of an overall risk management. IDRA-P4 IDRA-P5 GVPO-P1 GVPO-P6 GVRM-P1 GVRM-P2 GVRM-P3 PRPO-P5.
NIST has co-developed SP 800-63-3 with the community feedback was solicited via GitHub and email to ensure that it helps organizations implement effective digital identity services reflects available technologies in the market and makes room for innovations on the horizon. This publication is available free of charge from. NIST Special Publication 800 -37 Revision 2.
Managing Information Security Risk Organization Mission and Information System View Multi-level risk management approach Implemented by the Risk Executive Function Enterprise Architecture and SDLC Focus Supports all steps in the RMF. Special Publication 800-39 provides a structured yet flexible approach for managing information security risk that is intentionally broad-based with the specific details of assessing responding to and monitoring risk on an ongoing basis provided by other supporting NIST security standards and guidelines. This publication describes the Risk Management Framework RMF and provides guidelines for applying the RMF to information systems and organizations.
National Institute of Standards and Technology Special Publication 800-63-3.