Ad Risk management solution to identify analyze prioritize and respond to risks. Assess risk create your risk registry plan mitigations and perform management reviews.
 Security Risk Management Cycle With Security Decay Adjusted From The Download Scientific Diagram
Security Risk Management Cycle With Security Decay Adjusted From The Download Scientific Diagram
Risk management involves comprehensive understanding analysis and risk mitigating techniques to ascertain that organizations achieve their information security objective.
Risk management security. Ad Explore new cybersecurity trends technologies and approaches. Provides protection from events that are detrimental to both the company and the environment. Information security risk management or ISRM is the process of managing risks associated with the use of information technology.
The Gartner Security Risk Management Summit 2021 brings together security risk and identity and access management IAM decision makers looking to adapt and evolve their organization through disruption and uncertainty navigate risks and prioritize investments. Information security refers to the processes or tools that have been deployed or designed. Ad Navigate Uncertain Times Get Financial Risk Manager FRM Certified.
Other important benefits of risk management include. What is Information Security Risk Management. Increases the stability of business operations while also decreasing legal liability.
Security risk management in a public cloud involves organizations securing their own data with software while the cloud provider secures the underlying infrastructure. Risk is fundamentally inherent in every aspect of information security decisions and thus risk management concepts help aid each decision to be effective in nature. GARP Is the Worlds Leading Professional Organization for Financial Risk Managers.
Together we can make networks devices and applications more secure. Creates a safe and secure work environment for all staff and customers. It involves identifying assessing and treating risks to the confidentiality integrity and availability of an organizations assets.
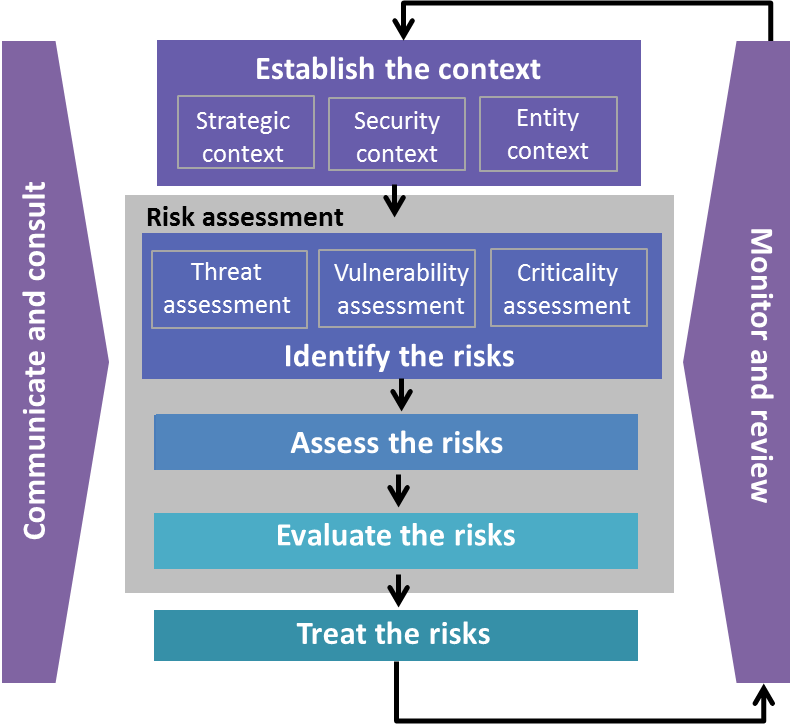
Security risk management Security risk management provides a means of better understanding the nature of security threats and their interaction at an individual organizational or community level Standards Australia 2006 p. GARP Is the Worlds Leading Professional Organization for Financial Risk Managers. Generically the risk management process can be applied in the security risk management context.
The goal of most security programs is to reduce risk. Follow news coming from the Gartner Security Risk Management Summit on the Gartner Newsroom and. Assess risk create your risk registry plan mitigations and perform management reviews.
Ad Risk management solution to identify analyze prioritize and respond to risks. Our highly trained experienced and professional security team are fully licenced to provide a range of solutions and security services to suit any scale of project. Change Management In IT Security And Risk Management.
Avoidance reduction spreading transfer and acceptance. Risk factors in the cloud. Risk Management Security provide first-class site security services for the public and private sectors throughout Buckinghamshire Berkshire and Oxfordshire.
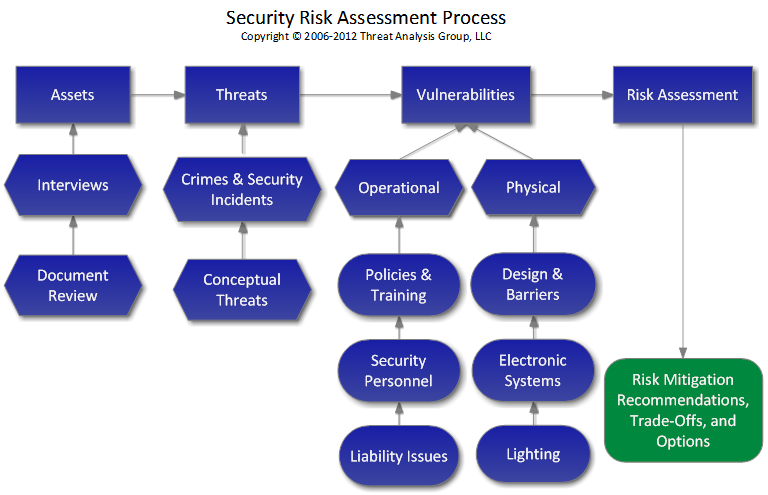
Security Risk Management Building an Information Security Risk Management Program from the Ground Up. Our security risk assessment methodology is a holistic and logical process as seen in the flow chart below. Ad Navigate Uncertain Times Get Financial Risk Manager FRM Certified.
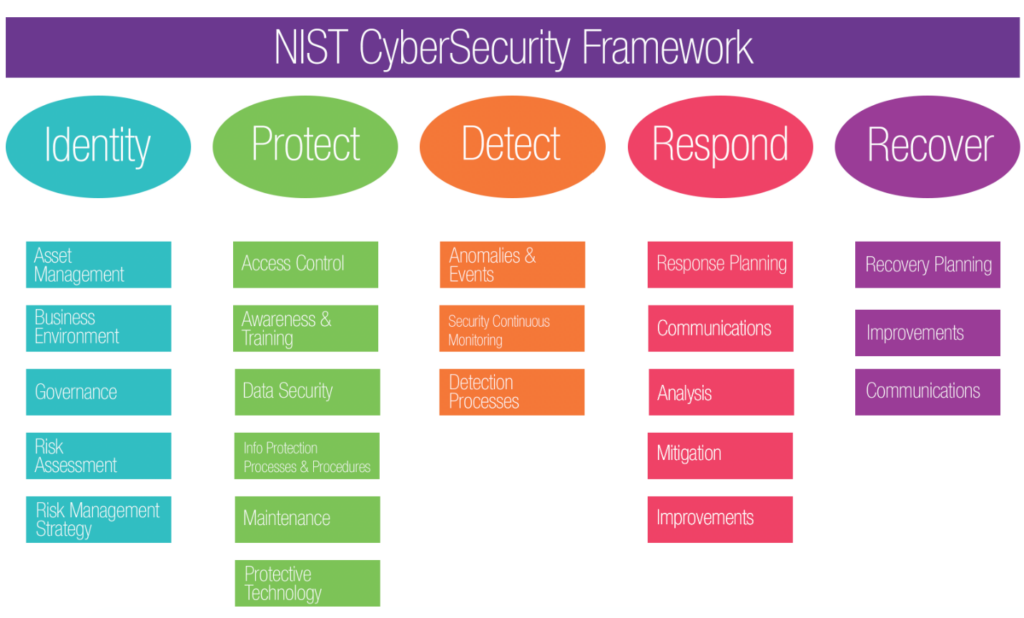
Ad Explore new cybersecurity trends technologies and approaches. Together we can make networks devices and applications more secure. The major components of Security and Risk.
Given a specific risk there are five strategies available to security decision makers to mitigate risk.
 Experienced Security Consultants Representing You Sikur Services A Security Risk Management Consulting Company
Experienced Security Consultants Representing You Sikur Services A Security Risk Management Consulting Company
 Enterprise Security Risk Management
Enterprise Security Risk Management
 3 Security Planning And Risk Management Protective Security Policy Framework
3 Security Planning And Risk Management Protective Security Policy Framework
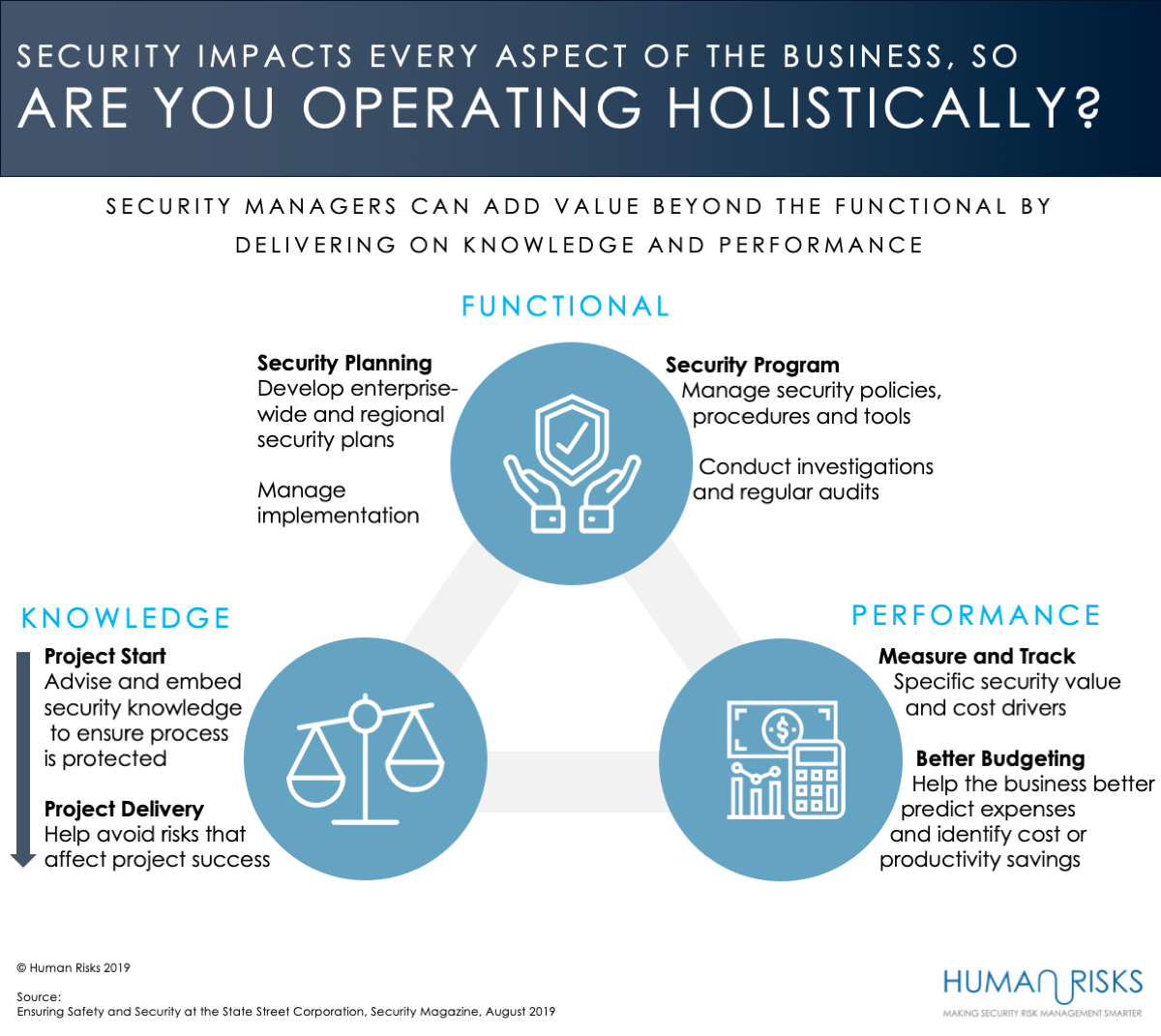
 What Are Your Top Security Risk Management Priorities For 2020 Human Risks
What Are Your Top Security Risk Management Priorities For 2020 Human Risks
 Security Risk Management Independent Security Consultants
Security Risk Management Independent Security Consultants
 How To Build An Effective Information Security Risk Management Program
How To Build An Effective Information Security Risk Management Program
 Information Security Risk Management Build A Strong Program
Information Security Risk Management Build A Strong Program
 Security Risk Management Services Security Bm Region 2
Security Risk Management Services Security Bm Region 2
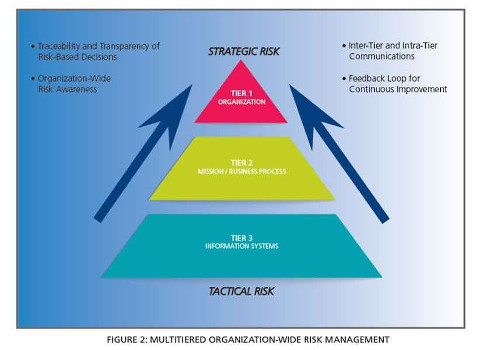 Control Engineering Cyber Security Risk Management How Secure Is Secure
Control Engineering Cyber Security Risk Management How Secure Is Secure
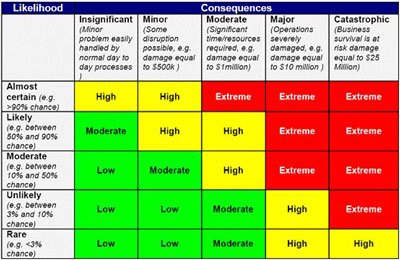 Cyber Security Risk Management Plans Securityri
Cyber Security Risk Management Plans Securityri
 People Management And Security Risk Management World Reliefweb
People Management And Security Risk Management World Reliefweb
 How To Assess And Mitigate Software Security Risks Today
How To Assess And Mitigate Software Security Risks Today
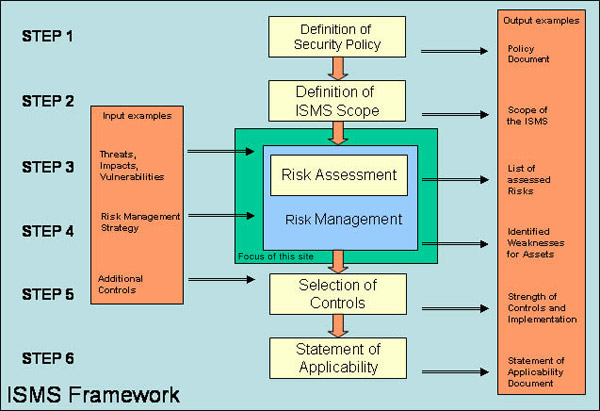
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.