Click on BitLocker Drive Encryption. This capability is known as.
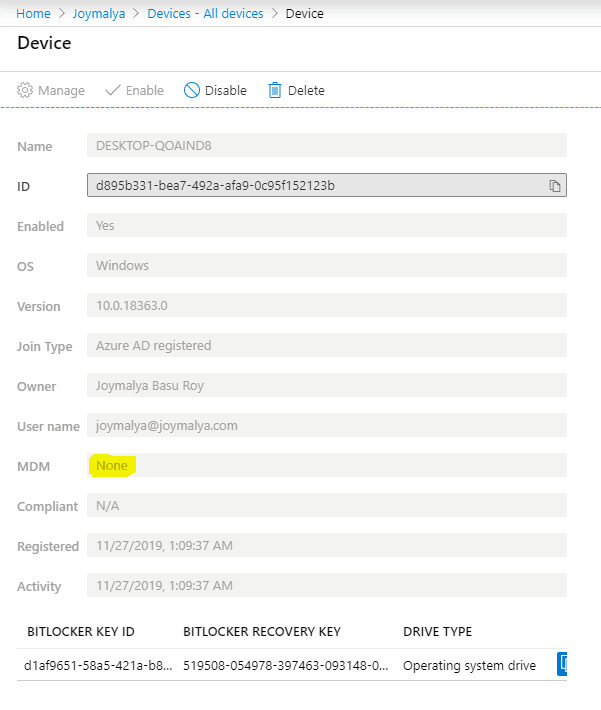 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
A message will be displayed stating that the drive.
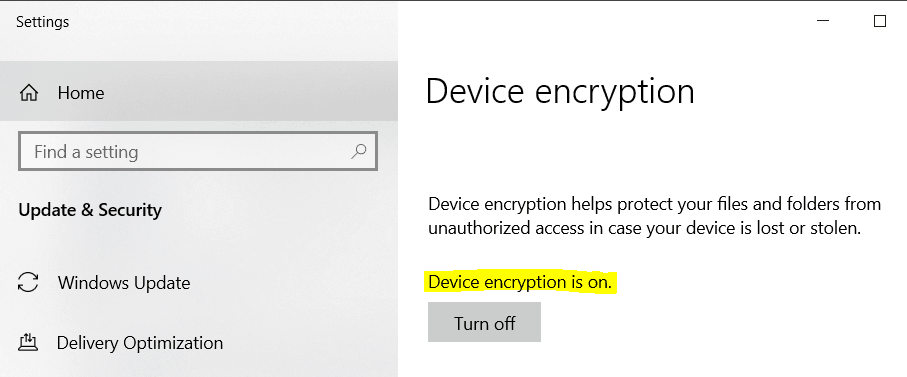
Bitlocker encryption can be deployed three ways. Via SCCM for existing computers. As already stated you cant actually start the blocker encryption directly from within active directory. The BitLocker Setup wizard provides administrators the ability to choose the Used Disk Space Only or Full encryption method when enabling BitLocker for a volume.
Encrypt the Exchange data volumes only. To resume the BitLocker protection on your device use these steps. For best security a PIN or password can be required at every startup in addition to TPM.
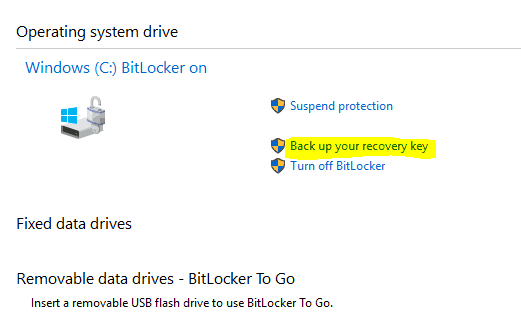
Three authentication mechanisms can be used as building blocks to implement BitLocker encryption. Look for the drive on which you want BitLocker Drive Encryption turned off and click Turn Off BitLocker. Manage-bde -protectors -get c.
To force the encryption of external drives activate Deny write access to removable drives not protected by BitLocker. After completing the system check if selected the BitLocker Drive Encryption Wizard will restart the computer to begin encryption. Users can check encryption status by checking the system notification area or the BitLocker control panel.
In order for computers to properly store the encryption keys in the MBAM database specific registry keys must be set. I wanted a way to automatically enable BitLocker with Group Policy without requiring user interaction and without requiring MBAM and figured a PowerShell script was the easiest way to do it. Ive demonstrated a way to securely deploy Windows 10 with encryption and enabled easy handling to add the PIN as additional pre-boot authentication for BitLocker.
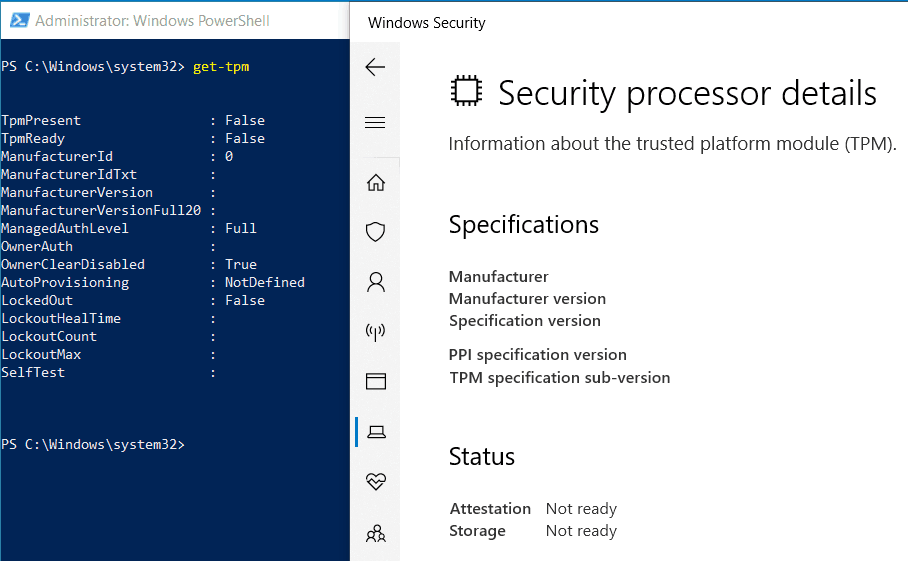
Implement BitLocker on CSVs and SANs Windows Server 2012 introduced the ability to apply BitLocker Drive Encryption on cluster shared volumes CSVs based in storage area network SAN shared storage. This mode uses the capabilities of TPM 12 hardware to provide for transparent user experiencethe. Encrypt the operating system volume as well as the Exchange data volumes utilizing either network unlock the Data Recovery Agent and PKI infrastructure or via TPM recommended approach.
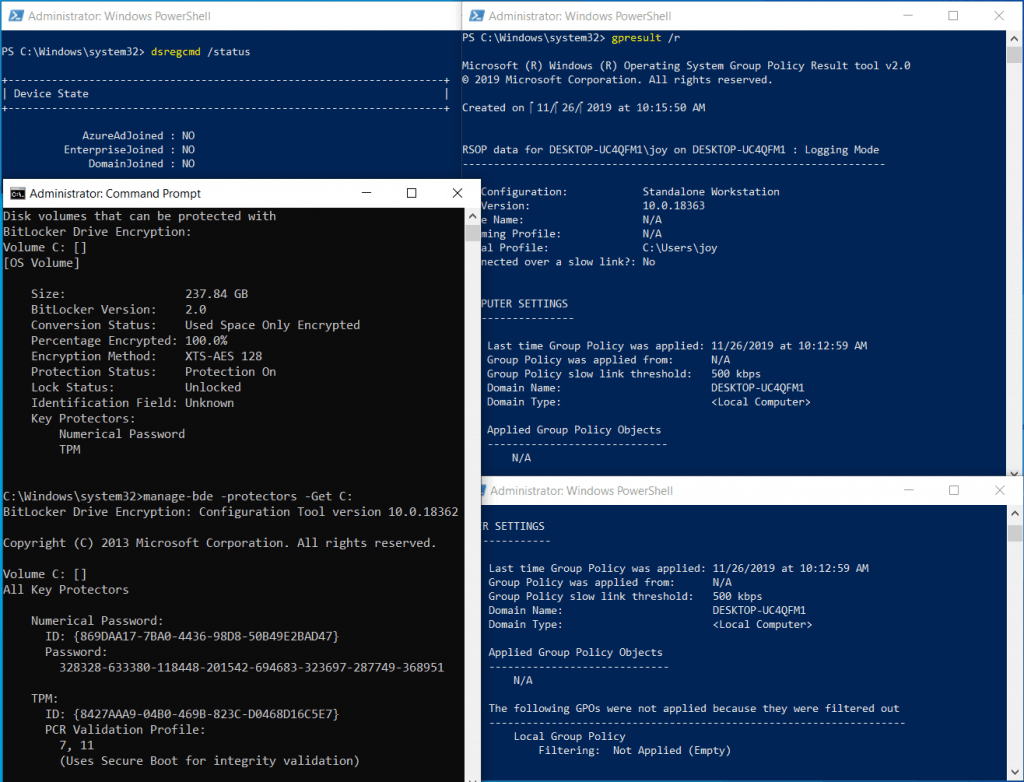
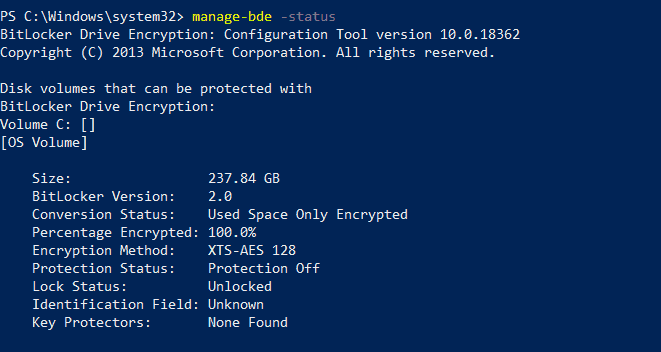
We can also check Key Protectors by running this command. However there is a solution to make the drive encryption silent with no user interaction. This can be problematic as users can defer the encryption indefinitely.
While both of the above scripts will work I chose the latter. Check if the encryption status equals FullyDecrypted If so add add a recovery password which is pushed to AD Enable Bitlocker with the TPM option to store the keys in the TPM. How can BitLocker be deployed.
Launching the BitLocker Setup wizard prompts for the authentication method to be used password. As we can see in the output BitLocker protection is On the Percentage Encrypted is 100 and our Encryption Method is XTS-AES 256. Verify that the Registry keys are configured.
Although this is a solution to set a startup PIN with Intune I really recommend to think twice as a PIN might not bring additional protection if the users are bugged by yet another PIN for the system. These keys are set via GPO. Administrators can use the new BitLocker Group Policy setting to enforce either Used Disk Space Only or Full disk encryption.
Specifically the full requirements were as follows. Identify which of the descriptions best describes the Computer and User authentication method. Bitlocker will be deployed by IT administrators in two main ways.
Upon reboot users are required to enter the password chosen to boot into the operating system volume. BitLocker Encryption can be deployed three ways. However if you are running Configuration Manager 2002 and below you will notice that Bitlocker prompts the user to encrypt the drive.
Manually via Active Directory Domain Services AD DS via cloud-based management with Azure Active Directory Azure AD and Microsoft Intune or the Microsoft-recommended way with Microsoft BitLocker Administration and Monitoring MBAM. Via DITR Lite Touch imaging for new computers being joined to the WIN domain. There are multiple ways you can deploy BitLocker on Exchange servers.
Of course this now means that you can deploy BitLocker Drive Encryption in local VMs the very same way you do in host hardware including requiring TPM. Click Start click Control Panel click System and Security and then click BitLocker Drive Encryption. Your organization has three options for managing BitLocker.
The script will need to place in a location where client machines can reach it for example the SYSVOL share. From here you can deploy your policies. It is possible to use a scheduled task on your laptops - which can be deployed via group policy preferences - to start the encryption process and pass in the required parameters.
Enforcing encryption The BitLocker To Go settings can be found under Computer Configuration Policies Administrative Templates Windows Components BitLocker Drive Encryption Removable Data Drives. Click on System and Security.
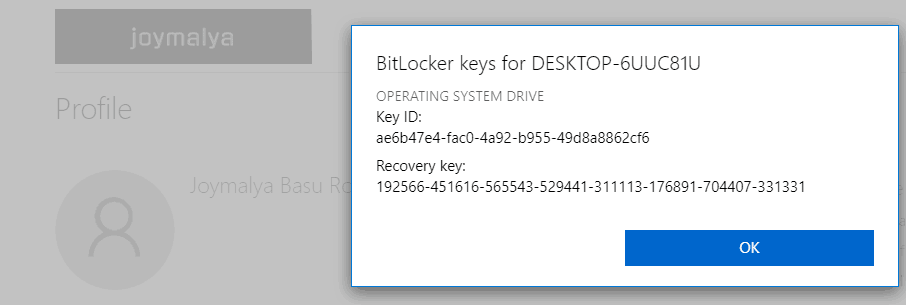 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Deploy Bitlocker For Your Business In The Right Way Edge It
Deploy Bitlocker For Your Business In The Right Way Edge It
 Micro Final Flashcards Quizlet
Micro Final Flashcards Quizlet
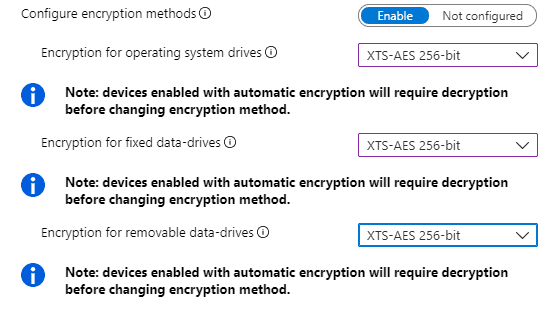 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Drag And Drop The Check Mark Bitlocker Encryption Can Be Deployed Three Ways Identify Which Of The Brainly Com
Drag And Drop The Check Mark Bitlocker Encryption Can Be Deployed Three Ways Identify Which Of The Brainly Com
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
 Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog
Device Encryption Bitlocker Made Effortless Part 2 Htmd Blog

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.